DDoS Attack
What is a DDOS Attack?
Introduction:
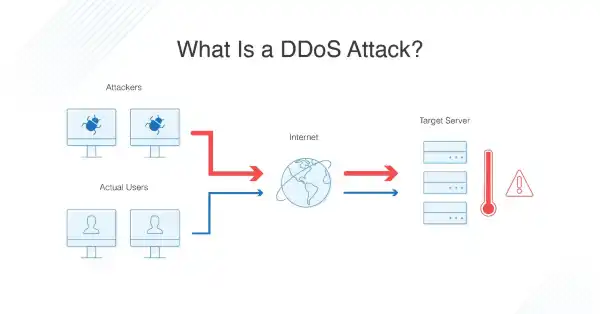
A Distributed Denial of Service (DDoS) attack is a malicious attempt to disrupt the regular functioning of a network, service, or website by overwhelming it with a flood of traffic. DDoS attacks leverage multiple compromised computers, forming a network of bots (botnet), to generate an excessive volume of requests or data, ultimately causing a system to become unavailable to its intended users.
Definition:
DDoS attacks involve overwhelming a target system with traffic from multiple sources, making it difficult to distinguish legitimate requests from malicious ones. Attackers exploit vulnerabilities in network protocols, application layers, or infrastructure to orchestrate these attacks.
Analogy:
Picture a traffic jam on a highway caused by a swarm of coordinated vehicles intentionally clogging the lanes. Similarly, a DDoS attack congests a network with an overwhelming volume of traffic, disrupting normal operations.
Further Description:
DDoS attacks can take various forms, targeting different layers of a network:
Volumetric Attacks: Flood the network with a high volume of traffic, consuming available bandwidth and causing congestion.
Protocol Attacks: Exploit vulnerabilities in network protocols, such as TCP/IP, overwhelming targeted servers with connection requests.
Application Layer Attacks: Target specific applications or services, exploiting weaknesses in the software to exhaust server resources.
Why DDoS Attacks Are Executed:
Extortion: Attackers may demand payment to stop the DDoS attack, threatening prolonged disruption.
Competitive Advantage: Businesses may sabotage competitors’ online presence to gain a competitive edge.
Hacktivism: Activists may launch DDoS attacks to promote their cause, expressing dissent or disagreement.
Distraction: DDoS attacks can serve as a diversion to divert attention from other malicious activities, such as data theft.
Mitigation Strategies:
Traffic Filtering: Employ firewalls and intrusion detection systems to filter out malicious traffic.
Content Delivery Networks (CDNs): Distribute content across multiple servers globally, reducing the impact of volumetric attacks.
Load Balancing: Distribute incoming network traffic across multiple servers, preventing a single point of failure.
Incident Response Planning: Develop and implement a comprehensive incident response plan to mitigate the impact of an ongoing attack.
Key Takeaways:
- DDoS attacks aim to disrupt the normal functioning of a network or service by overwhelming it with a flood of traffic.
- Attackers use botnets and various techniques to exploit vulnerabilities in networks, applications, or infrastructure.
- Mitigation strategies include traffic filtering, content delivery networks, load balancing, and incident response planning.
- DDoS attacks may have different motivations, including extortion, competitive advantage, hacktivism, and distraction.
Table of Contents