Hashing
What is Hashing?
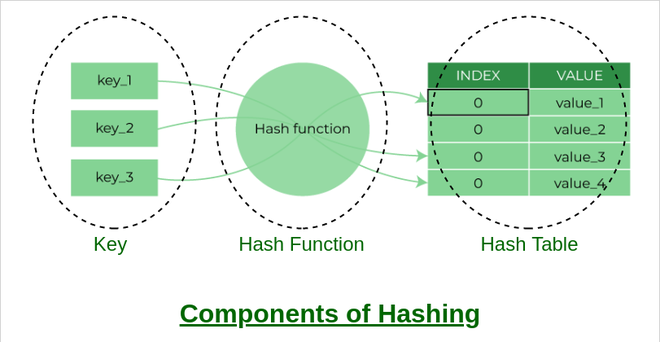
Definition:
Hashing is a fundamental concept in computer science and cryptography that involves transforming input data into a fixed-size string of characters using a mathematical algorithm. The resulting string, known as a hash value or hash code, is unique to the input data and serves various purposes, including data integrity verification, password storage, and digital signatures.
Analogy:
Think of hashing as a fingerprinting process for data. Just as each individual has a unique fingerprint, each piece of data generates a distinct hash value. Like fingerprints, hash values provide a means of identification and verification, ensuring the integrity and authenticity of the original data.
Further Description:
- Hashing algorithms operate by taking input data of any size and producing a fixed-length output, typically represented as a hexadecimal string. These algorithms are designed to be deterministic, meaning that the same input will always produce the same hash value.
Key Characteristics of Hashing:
Deterministic: Hashing algorithms consistently generate the same hash value for a given input, ensuring predictability and reliability.
Collision Resistance: A good hashing algorithm minimizes the likelihood of two different inputs producing the same hash value, known as a collision. Collision resistance is essential for maintaining data integrity and security.
Irreversibility: Hash functions are designed to be one-way, meaning that it is computationally infeasible to reverse-engineer the original input from its hash value. This property is crucial for securely storing passwords and sensitive information.
Fixed Output Size: Hashing algorithms produce hash values of a fixed length, regardless of the size of the input data. This uniformity facilitates efficient storage and comparison of hash values.
Why is Hashing Important?
Data Integrity: Hashing ensures the integrity of data by providing a reliable means of verifying that the data has not been altered or tampered with.
Password Security: Hashing is commonly used to store passwords securely. Instead of storing plaintext passwords, systems store hashed representations, making it difficult for attackers to retrieve the original passwords.
Data Deduplication: Hashing facilitates the identification and elimination of duplicate data by comparing hash values. This process is commonly used in data storage and backup systems to optimize storage space.
Digital Signatures: Hashing plays a critical role in digital signatures, where a hash value is encrypted with a private key to create a unique digital signature. The recipient can then use the sender’s public key to verify the signature’s authenticity.
Examples and Usage:
File Integrity Verification: Hashing algorithms such as SHA-256 are used to generate checksums for files, allowing users to verify the integrity of downloaded or transferred files.
Password Storage: Web applications commonly use hashing algorithms like bcrypt or PBKDF2 to securely store user passwords in databases.
Blockchain Technology: Hashing is a foundational concept in blockchain technology, where each block contains a hash value that links it to the previous block, creating a tamper-resistant chain of transactions.
Key Takeaways:
- Hashing involves transforming input data into a fixed-size hash value using a mathematical algorithm.
- Key characteristics include determinism, collision resistance, irreversibility, and fixed output size.
- Hashing is important for data integrity verification, password security, data deduplication, digital signatures, and blockchain technology.
- Examples of hashing applications include file integrity verification, password storage, and blockchain technology.
Table of Contents




